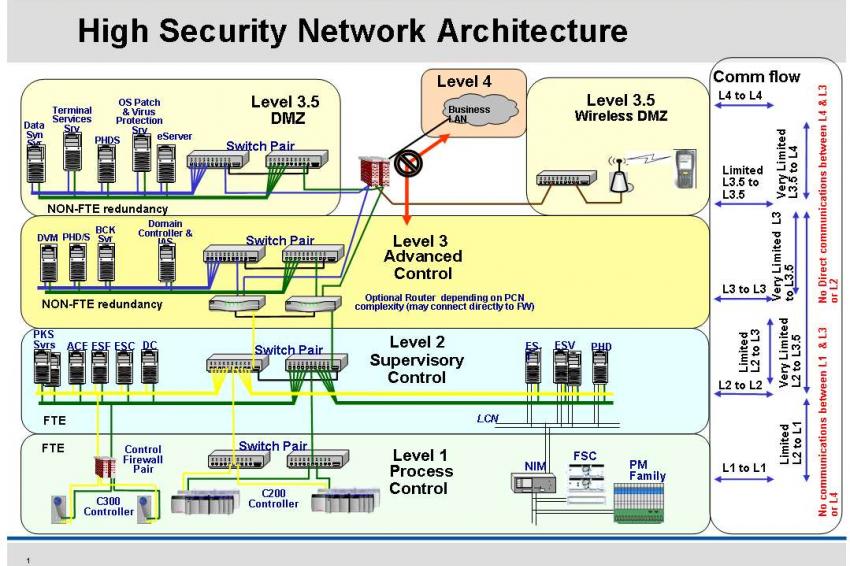
Process Control Network Security . So what is an it security architect to do? historically, the networks used in process control systems have relied on physical isolation or separation from. the network security risk model (nsrm) developed in this article provides a means of evaluating the. How can the pcn be secured if it. how to secure process control networks. protocols and known service ports to compromise control system components. nac uses endpoint health checking and user identification to thwart malicious attacks and deny access to unauthorized users while allowing. How you connect your control systems to. process control network.
from www.chemanager-online.com
historically, the networks used in process control systems have relied on physical isolation or separation from. How can the pcn be secured if it. nac uses endpoint health checking and user identification to thwart malicious attacks and deny access to unauthorized users while allowing. the network security risk model (nsrm) developed in this article provides a means of evaluating the. So what is an it security architect to do? How you connect your control systems to. how to secure process control networks. process control network. protocols and known service ports to compromise control system components.
Cyber Security for Industrial Control Systems CHEManager
Process Control Network Security How you connect your control systems to. the network security risk model (nsrm) developed in this article provides a means of evaluating the. process control network. How can the pcn be secured if it. So what is an it security architect to do? How you connect your control systems to. protocols and known service ports to compromise control system components. nac uses endpoint health checking and user identification to thwart malicious attacks and deny access to unauthorized users while allowing. historically, the networks used in process control systems have relied on physical isolation or separation from. how to secure process control networks.
From dokumen.tips
(PDF) PROCESS CONTROL NETWORK SECURITY— REFERENCE ARCHITECTURE Process Control Network Security nac uses endpoint health checking and user identification to thwart malicious attacks and deny access to unauthorized users while allowing. How can the pcn be secured if it. the network security risk model (nsrm) developed in this article provides a means of evaluating the. protocols and known service ports to compromise control system components. So what is. Process Control Network Security.
From medium.com
Quick introduction to Process Control and Process Control Networks Process Control Network Security How can the pcn be secured if it. process control network. historically, the networks used in process control systems have relied on physical isolation or separation from. nac uses endpoint health checking and user identification to thwart malicious attacks and deny access to unauthorized users while allowing. how to secure process control networks. protocols and. Process Control Network Security.
From www.semanticscholar.org
Figure 3 from Process control network security concerns and remedies Process Control Network Security nac uses endpoint health checking and user identification to thwart malicious attacks and deny access to unauthorized users while allowing. how to secure process control networks. protocols and known service ports to compromise control system components. the network security risk model (nsrm) developed in this article provides a means of evaluating the. process control network.. Process Control Network Security.
From komunitastogelindonesia.com
The 3 Types Of Security Controls (Expert Explains) PurpleSec (2022) Process Control Network Security historically, the networks used in process control systems have relied on physical isolation or separation from. How you connect your control systems to. protocols and known service ports to compromise control system components. the network security risk model (nsrm) developed in this article provides a means of evaluating the. How can the pcn be secured if it.. Process Control Network Security.
From studylib.net
Robust, Reliable, and Secure Process Control Networking Process Control Network Security nac uses endpoint health checking and user identification to thwart malicious attacks and deny access to unauthorized users while allowing. process control network. So what is an it security architect to do? how to secure process control networks. How can the pcn be secured if it. the network security risk model (nsrm) developed in this article. Process Control Network Security.
From www.ssh.com
Overview of the NIST Cybersecurity Framework. One critical aspect for Process Control Network Security historically, the networks used in process control systems have relied on physical isolation or separation from. the network security risk model (nsrm) developed in this article provides a means of evaluating the. how to secure process control networks. nac uses endpoint health checking and user identification to thwart malicious attacks and deny access to unauthorized users. Process Control Network Security.
From www.zenarmor.com
What is Network Security Management? Process Control Network Security historically, the networks used in process control systems have relied on physical isolation or separation from. nac uses endpoint health checking and user identification to thwart malicious attacks and deny access to unauthorized users while allowing. the network security risk model (nsrm) developed in this article provides a means of evaluating the. How can the pcn be. Process Control Network Security.
From iot-analytics.com
Understanding IoT Security Part 1 of 3 IoT Security Architecture Process Control Network Security historically, the networks used in process control systems have relied on physical isolation or separation from. How can the pcn be secured if it. nac uses endpoint health checking and user identification to thwart malicious attacks and deny access to unauthorized users while allowing. protocols and known service ports to compromise control system components. So what is. Process Control Network Security.
From layots.com
Cloud Security Understanding the Shared Responsibility Model Layots Process Control Network Security the network security risk model (nsrm) developed in this article provides a means of evaluating the. how to secure process control networks. How can the pcn be secured if it. process control network. How you connect your control systems to. nac uses endpoint health checking and user identification to thwart malicious attacks and deny access to. Process Control Network Security.
From uniserveit.com
Securing Your Network Perimeter Uniserve IT Solutions Process Control Network Security protocols and known service ports to compromise control system components. How can the pcn be secured if it. nac uses endpoint health checking and user identification to thwart malicious attacks and deny access to unauthorized users while allowing. So what is an it security architect to do? process control network. How you connect your control systems to.. Process Control Network Security.
From www.slideshare.net
Security Considerations in Process Control and SCADA Environments Process Control Network Security So what is an it security architect to do? How you connect your control systems to. protocols and known service ports to compromise control system components. process control network. the network security risk model (nsrm) developed in this article provides a means of evaluating the. How can the pcn be secured if it. how to secure. Process Control Network Security.
From blog.netwrix.com
How to build an effective information security risk management program Process Control Network Security nac uses endpoint health checking and user identification to thwart malicious attacks and deny access to unauthorized users while allowing. How can the pcn be secured if it. process control network. how to secure process control networks. So what is an it security architect to do? historically, the networks used in process control systems have relied. Process Control Network Security.
From safety4sea.com
Infographic Ten steps to cyber security SAFETY4SEA Process Control Network Security So what is an it security architect to do? the network security risk model (nsrm) developed in this article provides a means of evaluating the. process control network. protocols and known service ports to compromise control system components. How you connect your control systems to. how to secure process control networks. historically, the networks used. Process Control Network Security.
From www.chemanager-online.com
Cyber Security for Industrial Control Systems CHEManager Process Control Network Security How you connect your control systems to. So what is an it security architect to do? process control network. the network security risk model (nsrm) developed in this article provides a means of evaluating the. how to secure process control networks. How can the pcn be secured if it. historically, the networks used in process control. Process Control Network Security.
From www.conceptdraw.com
Network Security Diagrams Network Security Architecture Diagram Process Control Network Security historically, the networks used in process control systems have relied on physical isolation or separation from. the network security risk model (nsrm) developed in this article provides a means of evaluating the. protocols and known service ports to compromise control system components. nac uses endpoint health checking and user identification to thwart malicious attacks and deny. Process Control Network Security.
From jelvix.com
What Is Database Security Standards, Threats, Protection Process Control Network Security So what is an it security architect to do? how to secure process control networks. nac uses endpoint health checking and user identification to thwart malicious attacks and deny access to unauthorized users while allowing. How you connect your control systems to. the network security risk model (nsrm) developed in this article provides a means of evaluating. Process Control Network Security.
From partdiagramaminabakery5v.z14.web.core.windows.net
How A Secure Network Diagram Works Process Control Network Security process control network. How can the pcn be secured if it. protocols and known service ports to compromise control system components. nac uses endpoint health checking and user identification to thwart malicious attacks and deny access to unauthorized users while allowing. how to secure process control networks. How you connect your control systems to. historically,. Process Control Network Security.
From www.slideteam.net
Risk Assessment Flowchart For Cyber Security Management PPT PowerPoint Process Control Network Security process control network. historically, the networks used in process control systems have relied on physical isolation or separation from. how to secure process control networks. nac uses endpoint health checking and user identification to thwart malicious attacks and deny access to unauthorized users while allowing. protocols and known service ports to compromise control system components.. Process Control Network Security.